In my previous post i have introduced the topic " How to hack the wifi or wireless Networks" in which i have explained the various wireless scanning tools with their download links. I will explain you how to use them. So we will discuss scanning of wireless networks so that we can get the list of wireless networks around us and we can try our hacks on them. So guys lets continue Hacking Wireless Networks - Tutorial 2.
in previous post i have given you the list of topics that we cover in hacking wireless networks so lets continue the second topic.
2. Scanning the Wireless Networks or WiFi Networks
What is meant by scanning wireless networks?
First of all we have to locate all the wireless networks around us. For this we have to do the scan for wireless networks its pity similar like we scan with antivirus for viruses in our system. Similarly we look for wireless networks around us with wireless scanning tools that i have mentioned in previous post.
in this i have mentioned a lot of hack tools to scan the wireless networks but as i have said earlier my favorite is NetStumbler. Let's discuss now how to use NetStumbler?
Download NetStumbler from previous post:
How to use NetStumbler for Scanning Wireless Networks?
1. Download the NetStumbler and Install it.
2. Run the NetStumbler. Then it will automatically starts scanning the wireless Networks around you.
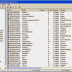
3. Once its completed, you will see the complete list of wireless networks around you as shown in the snapshot below:
| List of Wireless Networks Scanned by NetStumbler |
There you will see different columns such as MAC, SSID, SPEED, VENDOR, TYPE and much more...
4. Now select anyone of the MAC address that you wish to hack and want to explore more about that. If you click on the MAC address of one of the discovered wireless networks under channels, you will see a graph that shows the wireless network’s signal strength. The more green and the less spaces are there,it indicates better is signal strength.
5. As you can see NetStumbler provides a lot more than just the name (SSID) of the wireless network. It provides the MAC address, Channelnumber, encryption type, and a bunch more. All of these come in use when we decides that we wants to get in the secured network by cracking the encryption.
There are two most common types of Encryption Methods used by Wireless Networks:
a. WEP (Wired Equivalent Privacy) – WEP isn’t considered safe anymore. Many flaws have been discovered that allow hackers to crack a WEP key easily. I will explain how to hack the WEP in next tutorial so guys keep reading..
b. WAP (Wireless Application Protocol) – WAP is the currently the most secure and best option to secure your wireless network. It’s not as easily cracked as WEP because the only way to retrieve a WAP key is
to use a brute-force or dictionary attack. If your key is secure enough, a dictionary attack won’t work and it could take decades to crack it if you brute-force it. This is why most hackers don’t even bother. But I will explain you smarter ways to hack WAP keys also rather than these noobish methods. I will explain this in my next consecutive tutorials. So guys keep visiting.
to use a brute-force or dictionary attack. If your key is secure enough, a dictionary attack won’t work and it could take decades to crack it if you brute-force it. This is why most hackers don’t even bother. But I will explain you smarter ways to hack WAP keys also rather than these noobish methods. I will explain this in my next consecutive tutorials. So guys keep visiting.
Thats all about scanning the wireless networks, if you want that i should explain the other tools then please post in comments. I can explain them in future on demand.
Now how can protect our wireless network from scanned by NetStumber.
How to Protect yourself from NetStumbler?
1. Don not broadcast your SSID.
2. Always try to use stronger passwords like atleast one digit, one special character, uppercase letters mixed with lowercase letters.
3. But second point doesn't matter much so try to use better encryption method i.e. WAP to password protect your wireless Network.




































.png)




